Area of expertise
Security protection – Time to act
Security protection is about protecting our society and our operations against unwanted influence, intrusions and attacks. The Swedish Security Protection Act (2018:585) and the Security Protection Ordinance (2021:955) apply to everyone who manages security-sensitive activities. It concerns a wider array of businesses than before, and the legislation clarifies that it applies to both public and privately owned businesses. On January 1 and December 1, 2021, the law has been expanded with provisions on, among other things, the transfer of security-sensitive operations and the supervisory authorities' possibilities for penalty fees.
In addition to this, all businesses have an interest in protecting their own information, for both for privacy and business integrity.
Why are security issues often under-prioritised?
We tend to take action if the probability is high, even if the consequences are small. Conversely, we tend to prepare poorly for risks with very low probability and potentially catastrophic consequences.
Another peculiarity that affects what gets done is the threshold for getting started. If it is unclear what to do and where to start, it is easy to postpone an issue in favor of something else. The risk of this increases the further away security issues are perceived from being core business.
To summarize, these biases often lead to underprioritization of security issues, both in terms of resource allocation and attention. This may be exploited by the forces against which we wish to protect ourselves.
Addressing the security issues
Amidst a detoriating security situation, focus is shifted towards security protection – the likelihood of something potentially catastrophic happening increases. Thus, it is easier than in a long time to get attention on security issues, both within organizations and among financiers.
Then only the second problem remains: How do you attack the issue in the best way?
The answer is gradual and systematic. First, the business's specific conditions are mapped and defined in a first stage, and then development measures are planned and managed in stage 2.
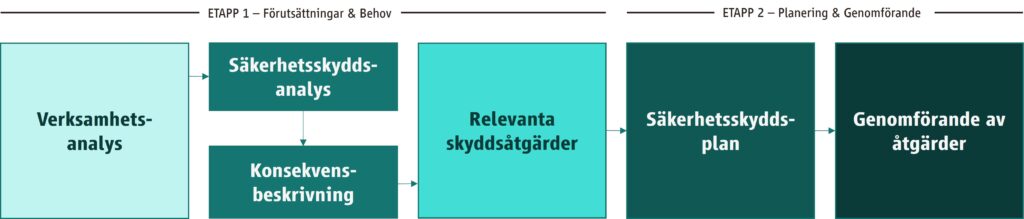
The first stage involves a combined analysis of the current situation, environment, risk and requirements, followed by defined protective measures. The second stage is about implementing the measures and implementing the security protection plan. The idea is that it should be clear and easy to do the right thing - while maintaining management confidence in the totality of the process.
Our offer
We support our clients in realizing a new way of working by:
- Contributing with methodology and a structured way of working
- Supplementing the client's organization with competence and experience
- Conducting business adapted security protection analysis and help prioritizing relevant protection measures
- Supporting in resourcing and planing the security protection function
- Supporting with change management and project management during implementation
